Phishing-As-A-Service: Making Cybercrime Easy to Commit
The Big Business of Renting Out Hacking Tools
Facts:
Phishing-as-a-Service (PhaaS) removes the technical barrier to cybercrime and is often marketed as a "complete solution for the beginner scammer”.
An investigation into one of these operations revealed that the site’s 67,000 users had made off with data from over 750,000 accounts, with an average of 65,000 accounts stolen per month.
A single campaign — consisting of a phishing page, a spam server, a 100,000-person email list, and a backend database to store stolen credentials — can be carried out for as little as $27. This is a quarter of the cost it would take to execute a standard phishing campaign.
With cybercriminals providing turnkey phishing services to anyone and everyone, the global loss from these kinds of attacks works out to be around $17,700 per minute...and it's only getting worse.
A Cautionary Tale
Welcome to HackShit: a PhaaS platform that provides several phishing services to the wannabe hacker, and also offers a marketplace to buy and sell such services.
Source: Netskope
In order to attract new subscribers, the site allows users to create a free account. From there, they can check out a handful of hacking tutorials and tricks for making easy money.
Source: Netskope
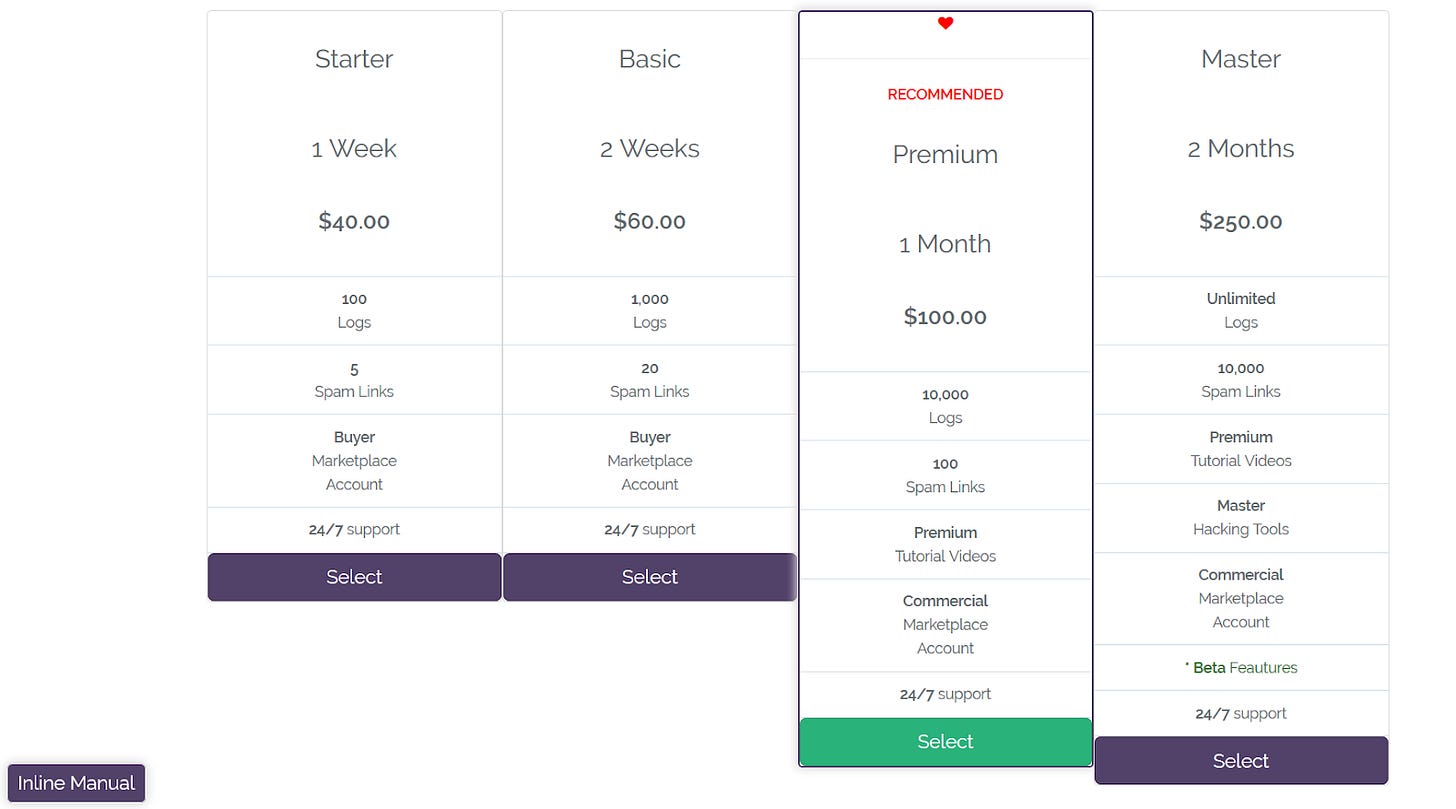
Once these users are ready to subscribe, they can check out HackShit’s pricing model and choose a tier that best fits their needs. Several types of payments are accepted; however, due to the nature of the site, the owners prefer bitcoin or PerfectMoney.
Source: Netskope
Now, the wannabe hacker is able to use his account to generate a unique phishing page from a selection of templates. This includes various social media, banking, retail, telecom, utility, gaming, and dating platforms. Once the subscriber has made his choice, HackShit will generate a link that he can then send to victims.

Source: Netskope
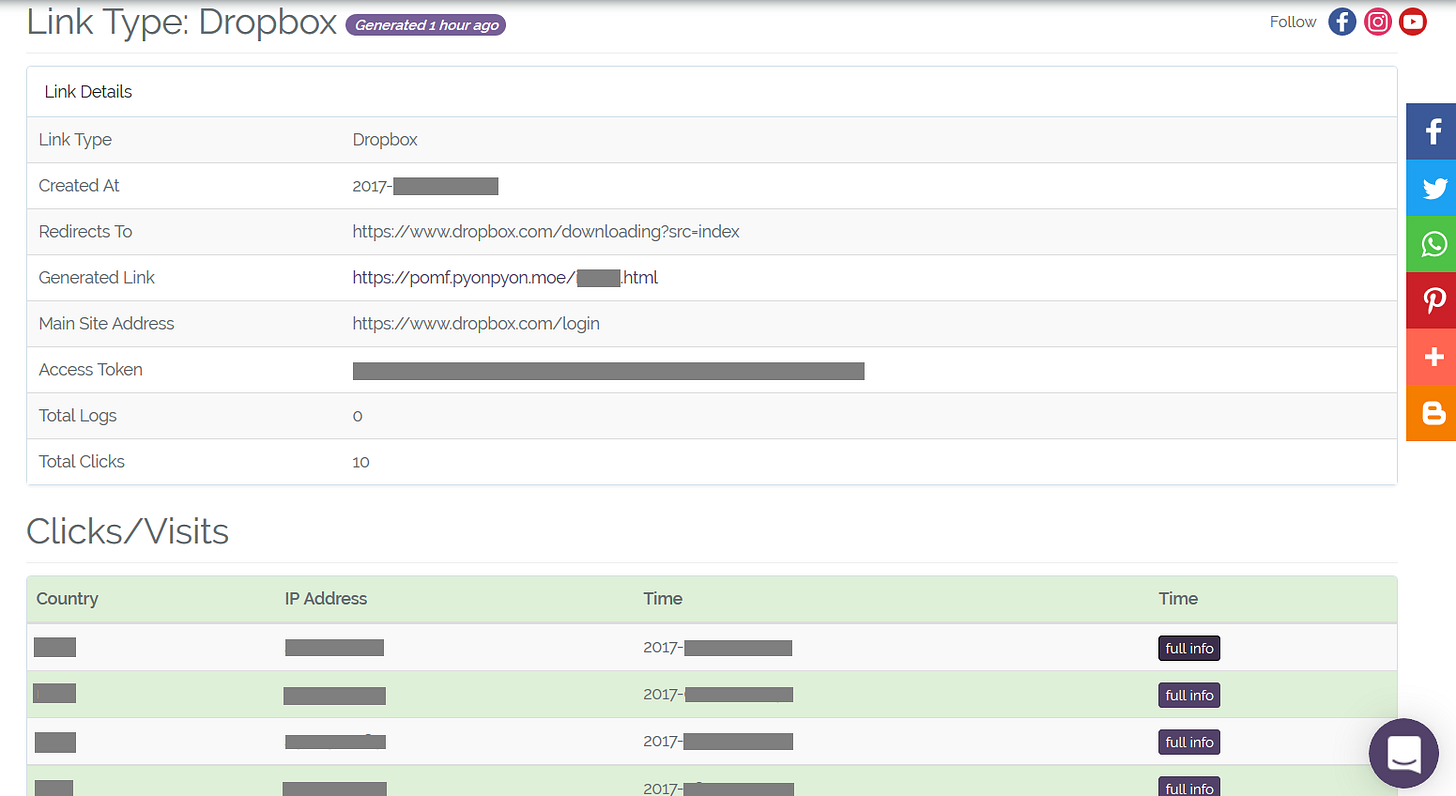
Details of the phishing campaign — along with successfully stolen credentials — are then stored on the user’s personal dashboard.
Source: Netskope
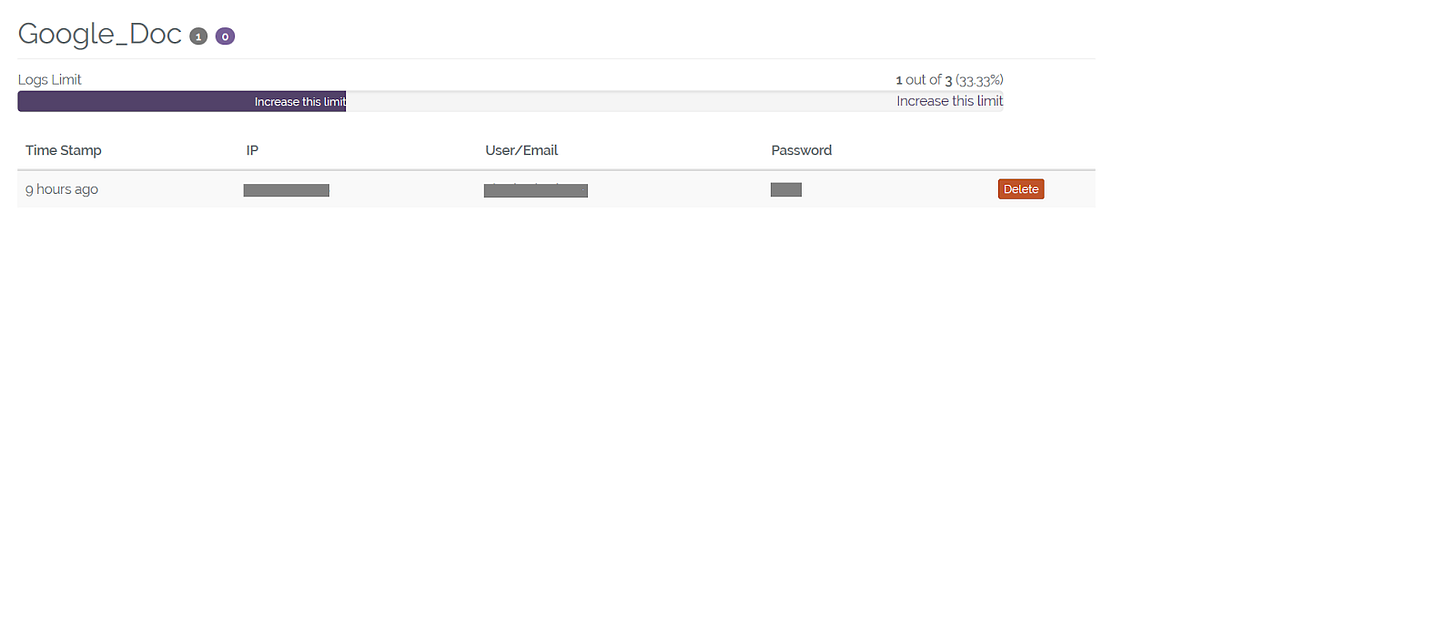
Source: Netskope
From here, the subscriber can either exploit these credentials for his own gain or sell them to interested buyers on HackShit’s marketplace.
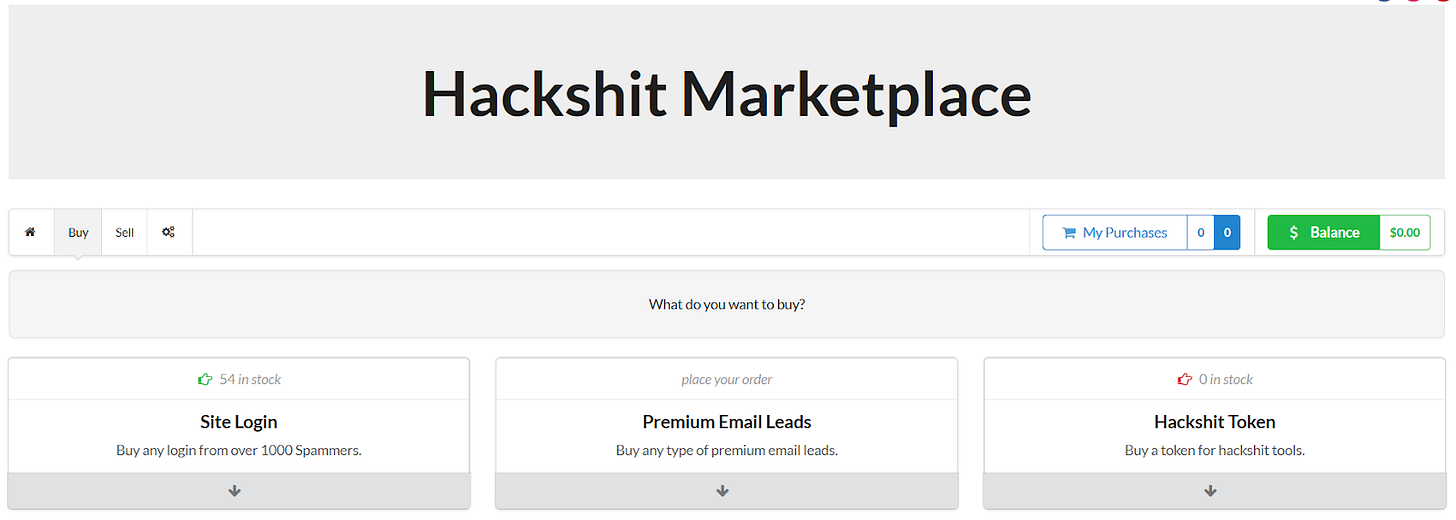
Source: Netskope
That said, cybercriminals who run successful phishing attacks do not usually take the risk of using the stolen accounts themselves. It is much safer for them to resell the accounts to other criminals, often charging around 10 percent of the total value of the stolen account.
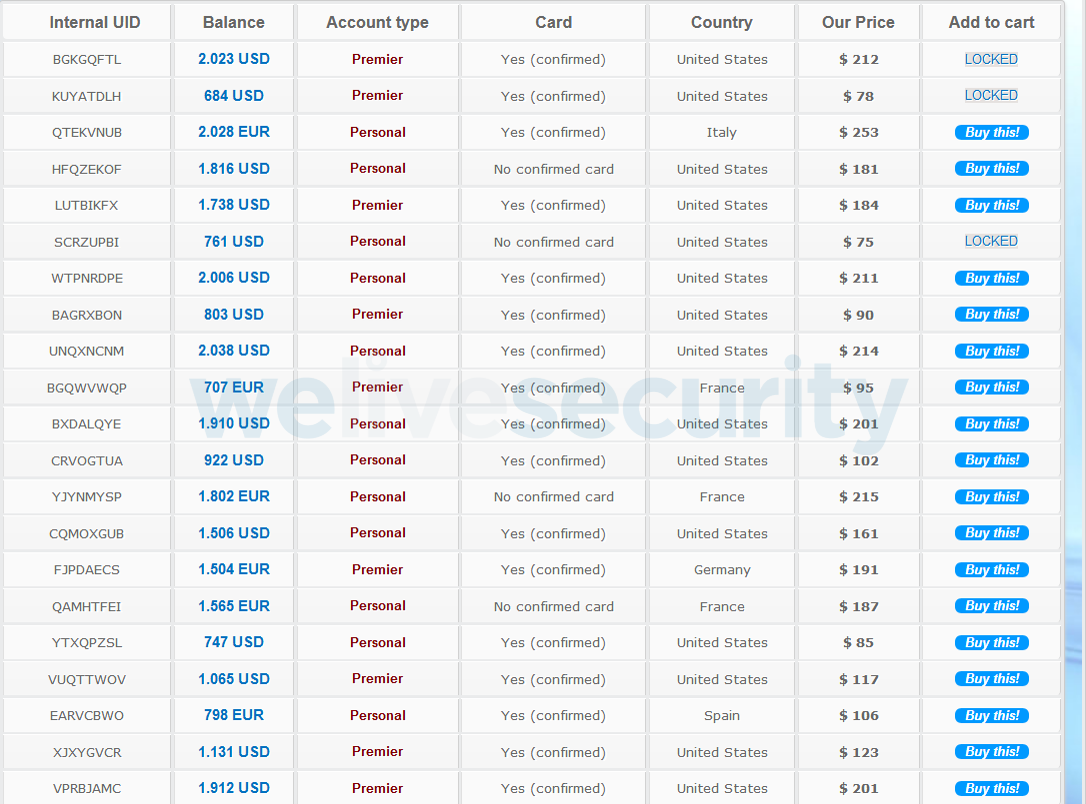
Source: ESET
Not bad for a rookie.
The Larger Scheme At Play
Phishing v.: an attempt to acquire sensitive information about a person online, typically by sending an email that appears to be from a legitimate source, but actually contains a link to a spoofed website that mimics the real one.
In the past, a major barrier of entry into the world of cybercrime was a lack of technical know-how. From planning and coding a campaign to hosting spoofed landing pages and selling the harvested data, the whole process was both tedious and time-consuming. The basic approach looked something like this:
Design the campaign. This includes identifying targets, choosing the best brands to spoof, deciding how the phish cycle will work (links versus attachments), and what will be done with the data collected.
Create the phishing email. This involves everything from setting up email servers, writing content, and creating the malicious links and/or attachments.
Set up the spoof website. Since phishing involves tricking a person into revealing details such as personal or financial information, the scammer needs to set up a spoofed login page to collect authentication credentials.
Profit from the collected data. Upon successful deployment of the phishing campaign, the scammer must now decide whether to sell these credentials on a darknet marketplace or use them to hijack the accounts and make his money that way.
Historically, a cybercriminal’s level of success depended heavily on his level of technical sophistication. However, when Phishing-as-a-Service (and other Crimeware-as-a-Service) platforms came onto the scene, they removed all of these steps. This included the ones that had previously befuddled and thwarted novice hackers without the proper knowledge, like anonymous web hosting and compromising servers. Thus, with the biggest barrier to entry out of the way, anyone with a bit of cash could deploy their own crimeware campaigns.
Welcome to the evolution of the cybercrime economy.
How It Works
Anyone can subscribe to Phishing-as-a-Service just like they would Netflix. In fact, by using a subscription model, enterprising cybercriminals have made it so that novice users have full access to professional phishing tools at an affordable price.
To get started:
Step One: Find a darknet marketplace that offers phishing campaigns as packaged products.
Step Two: Once there, register for an account and select a subscription tier. Proceed to the checkout page and pay with bitcoin.
Step Three: Now you have a selection of ready-made phishing kits to choose from. These kits are professionally designed to evade detection and improve success rates. That said, using phishing emails that mimic certain brands will yield better results than other brands. And emails that create a sense of urgency — such as “your account has been compromised” — also tend to do well.
While you might be pleased to have all of these phishing emails, malicious links, and hosted landing pages, — spoofed to look like the real deal — your subscription also places other tools at your disposal. The most important of which are evasion measures to ensure that your cybercrimes remain undetected. These include:
HTML Character Encoding. This means that some or all of a phishing page’s HTML code is encoded and displayed normally by web browsers. However, any security crawlers looking through the code will not be able to read the content — thereby missing keywords associated with phishing, such as “password” and “credit card”.
Content encryption. This tactic is similar to encoding, because the content in the code does not show up as readable text. But, rather than changing the representation of a word with character encoding, the entire content is encrypted — and a key is needed to decrypt and reveal the true content.
Inspection blocking is a technique where phishers employ block lists for connections — from specific IP addresses and hosts — in order to keep security systems and security analysts from evaluating and seeing the true nature of a phishing site. When someone on the block list tries to access the page, they are usually presented with a “404 page not found” message.
URLs in attachments. Rather than placing links to a phishing site in the body of emails, phishers will instead hide them in attachments — making detection more difficult. An example might be a simple PDF — composed of various images — that looks like a OneDrive document, with a single button that links to the phishing site.
Content injection is when malicious content is injected into the page of a legitimate website, thus changing part of that site’s content. From there, the unsuspecting user is taken to a phishing page, outside the legitimate website.
Legitimate cloud hosting. By hosting phishing websites on legitimate cloud services — such as Microsoft Azure or Amazon Web Services — phishers are able to present legitimate domains and SSL certificates. This, in turn, can trick even the most attentive user into thinking a given phishing page is trustworthy.
All of this to say that, when you rent a phishing kit or subscribe to a PhaaS platform, your success becomes the seller’s success. This means that any and all news of a successful Phishing-as-a-Service campaign will quickly spread across the cybercriminal community — resulting in more sales for the fraudsters behind the service. Therefore, they strive to offer the highest quality possible.
Step Four: No phishing campaign would be complete without a database of email addresses to spam. Fortunately, email lists are also included with your subscription (or available for a nominal fee) — thanks to a number of recent data breaches. These lists can be filtered based on user demographics, giving you a more targeted campaign.
Step Five: With all of the puzzle pieces in place, all you have to do is launch your campaign — with just a few clicks — and wait for victims to take the bait.
Take Steps to Protect Yourself
To reduce the chance of falling victim to a phishing attack, abide by the following guidelines:
Be smart and use logic while browsing online and checking your email. Resist the urge to click on any links or open any attachments, even if they appear to be from a trusted source. Furthermore, be wary of emails that ask you for sensitive information. Legitimate organizations, including your bank, will never request personal or financial details via email.
Watch out for shortened links. Cybercriminals often use Bit.ly and other URL shortening services to trick users into thinking they are clicking on a legitimate link. Instead, users are inadvertently directed to a fake site. To avoid this, place your mouse over a web link in an email to check whether you’re actually being sent to the right website. When in doubt, log in to the account in question by going to your web browser and typing in the known URL or by doing a simple Google search.
Does that email look suspicious? Read it again. Plenty of phishing emails are obvious. Many of them carry a series of typos, words in all caps, and exclamation marks. They may also have an impersonal greeting, such as Dear Customer or Dear Sir/Madam. This is done intentionally to get past spam filters and weed out those recipients who are too informed to fall for the con.
Be wary of threats and urgent deadlines. Sometimes a reputable company needs you to do something urgently. For example, in 2014, eBay asked its customers to change their passwords quickly after its data breach. However, more often than not, threats and urgency are used by phishers as scare tactics to prompt immediate action by users. These threats may include notices about a fine or advising you to do something to stop your account from being closed. If you receive a message like this, contact the company directly through their website or by phone. Do not trust the links provided in the email.
Final Notes and Updates
When people hear the terms “cybercrime” and “hacker”, they often bring to mind a cliché image of some hooded figure, hunched over a computer in his parent’s basement. In reality, cybercrime is carried out by sophisticated hacking gangs, operating just like any other legitimate business. From advertising and marketing to customer service and user agreements, PhaaS providers — hiding behind tools that offer a certain degree of anonymity — have put together a highly profitable criminal industry.
These platforms may be attractive to those looking to make a quick buck, but the real money is made by the providers of these services. Like many successful business models, they have taken something difficult and made it simple. Thus, making the world of cybercrime more accessible than ever before.
Useful Resources
A technical deep dive into PhaaS platforms:
https://www.netskope.com/blog/phishing-service-phishing-revamped
Imperva investigates the industrialization of PhaaS:
https://www.imperva.com/docs/Imperva-HII-phishing-made-easy.pdf
Report a phishing attack:
https://www.us-cert.gov/report-phishing
Editor’s Note: Have you been affected by fraud? Most people have, in some form or another. If you have a story you would like to share, we’re sure our readers would benefit from hearing it. Please send an email to editor@theconartist.pub detailing your experience, and we will be in touch. Your privacy and any wishes of anonymity will be respected.
Thanks for reading! If you haven’t already, consider joining our community to receive in-depth exposés on the latest scams, hoaxes, and other forms of fraud.


