Facts:
Slovakian security firm ESET recently discovered a phishing campaign that targets users via email.
The email claims that the PayPal account belonging to a user has experienced “unusual activity”, then prompts the target to login and secure their account.
In a series of steps, targets are asked to surrender several pieces of sensitive information, including credit card information and email login credentials.
After complying with these requests, the scam reassures the user that their account is now safe.
In reality, the con artists behind the attack can now use the information provided by the user to wreak havoc on their digital life and finances.
A Cautionary Tale
It’s Monday morning and you’ve just arrived at the office. After getting settled at your desk, you decide to check your email. Scrolling through your inbox, you notice a message from PayPal, alerting you to suspicious activity taking place on your account.
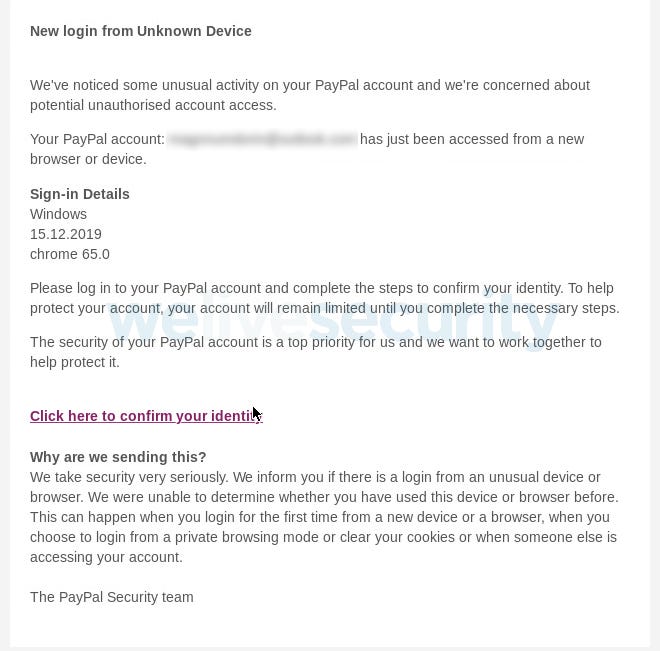
Source: ESET
The email prompts you to click on the link provided and secure the account. You think it over for a moment, but decide to click. After all, the email looks legitimate. The link redirects you to the following PayPal-branded page:
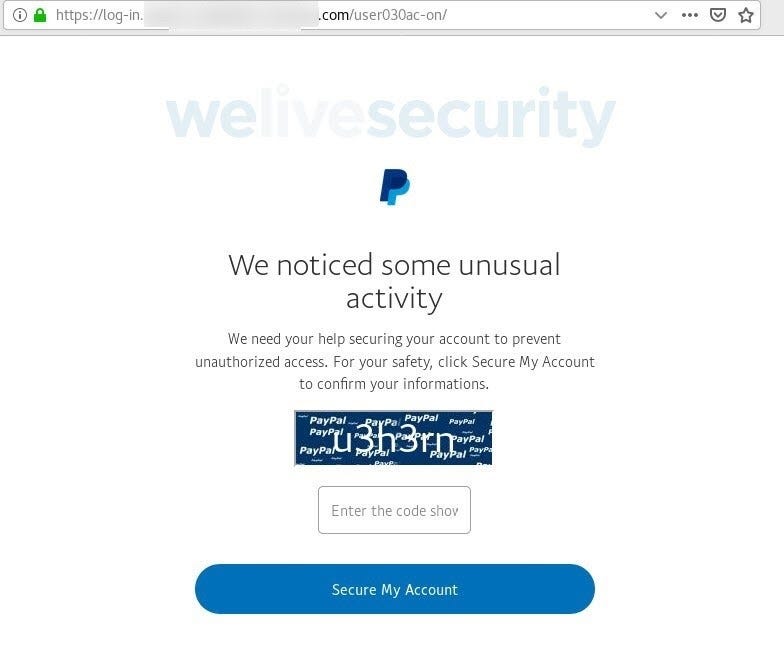
Source: ESET
You quickly glance over it. Looks harmless enough, you think to yourself. But a closer look would indicate otherwise. Little clues like the odd URL (not Paypal’s) and the unnecessary letter s on the word “information” are telltale signs that something isn’t quite right here. However, the email scares you into thinking that someone has gained unauthorized access to your PayPal account. You’d rather be safe than sorry, so you enter the CAPTCHA and follow the instructions on the next page.
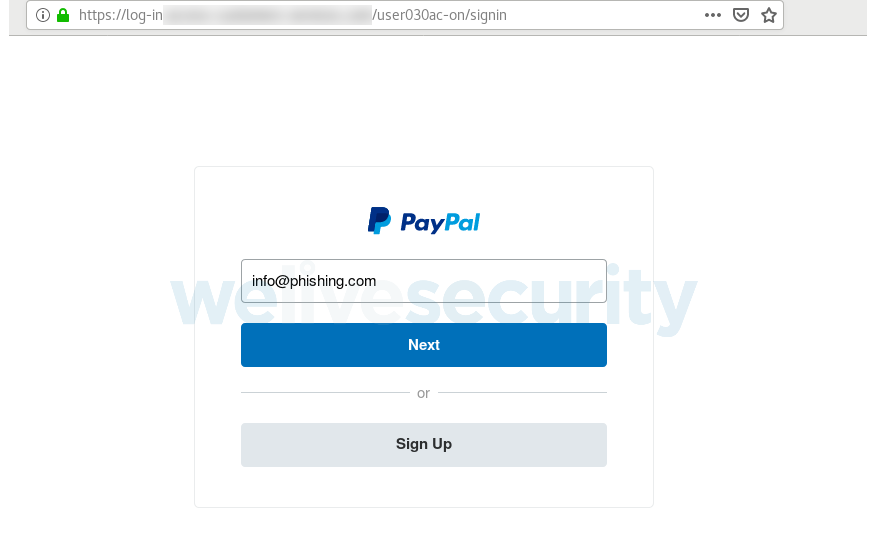
Source: ESET
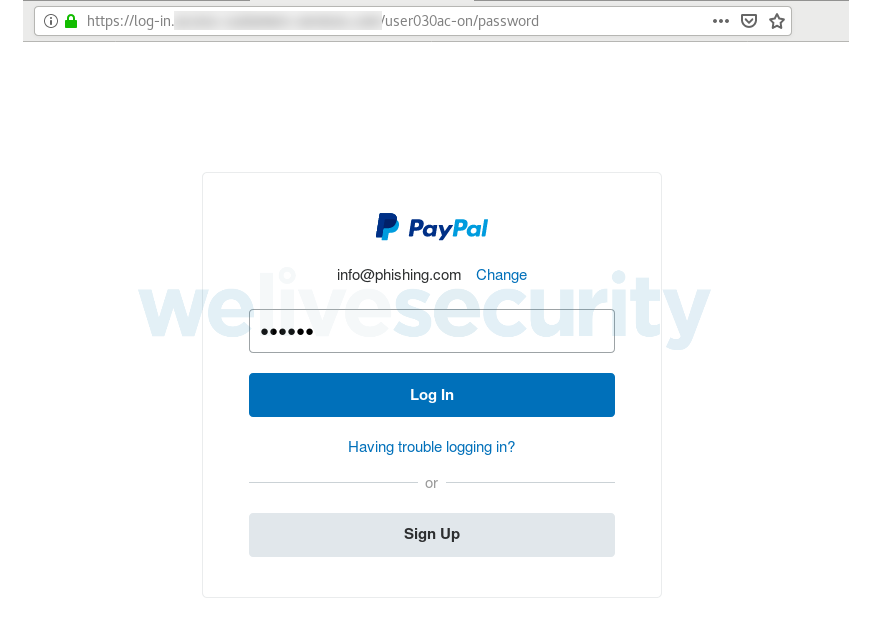
Source: ESET
After you’ve entered your PayPal username and password, you are told that the account has been limited. In order to restore your account, the website states that it needs to verify some personal information.
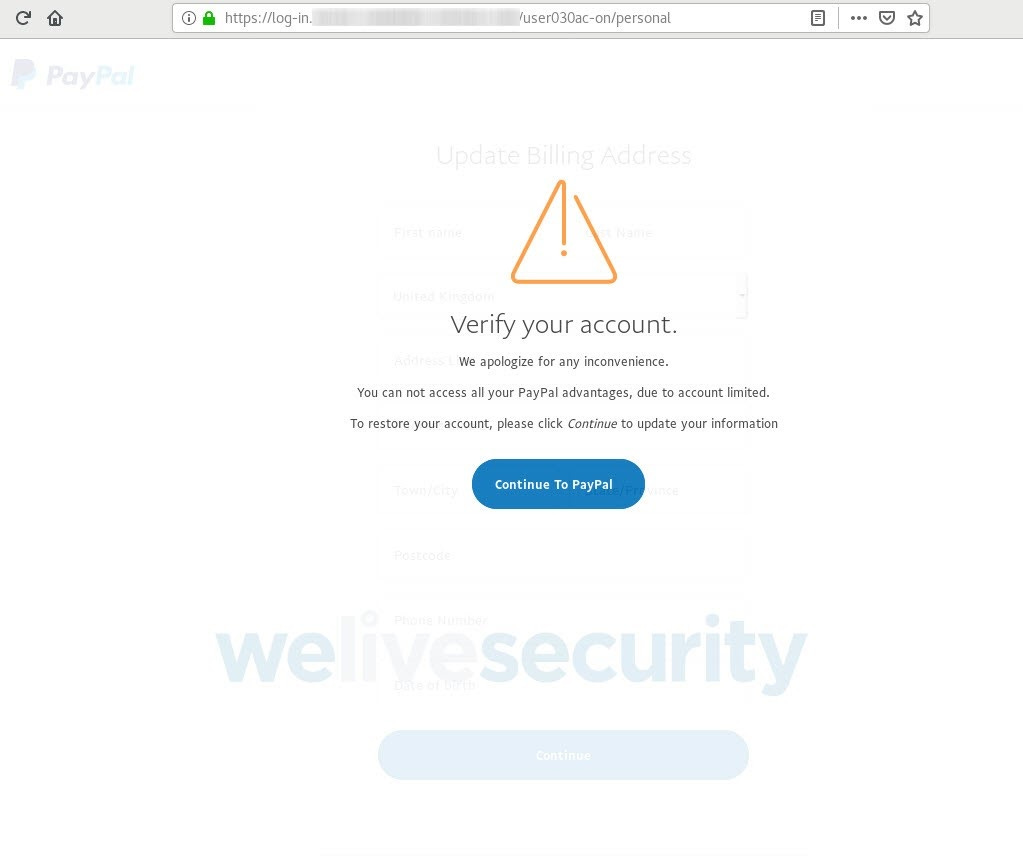
Source: ESET
At this point, you’ve already provided your login credentials to the platform. But now, the website asks for other details — starting with a request to update your billing address...and your date of birth? While this strikes you as a bit odd, you hand over the requested information and proceed to the next page.
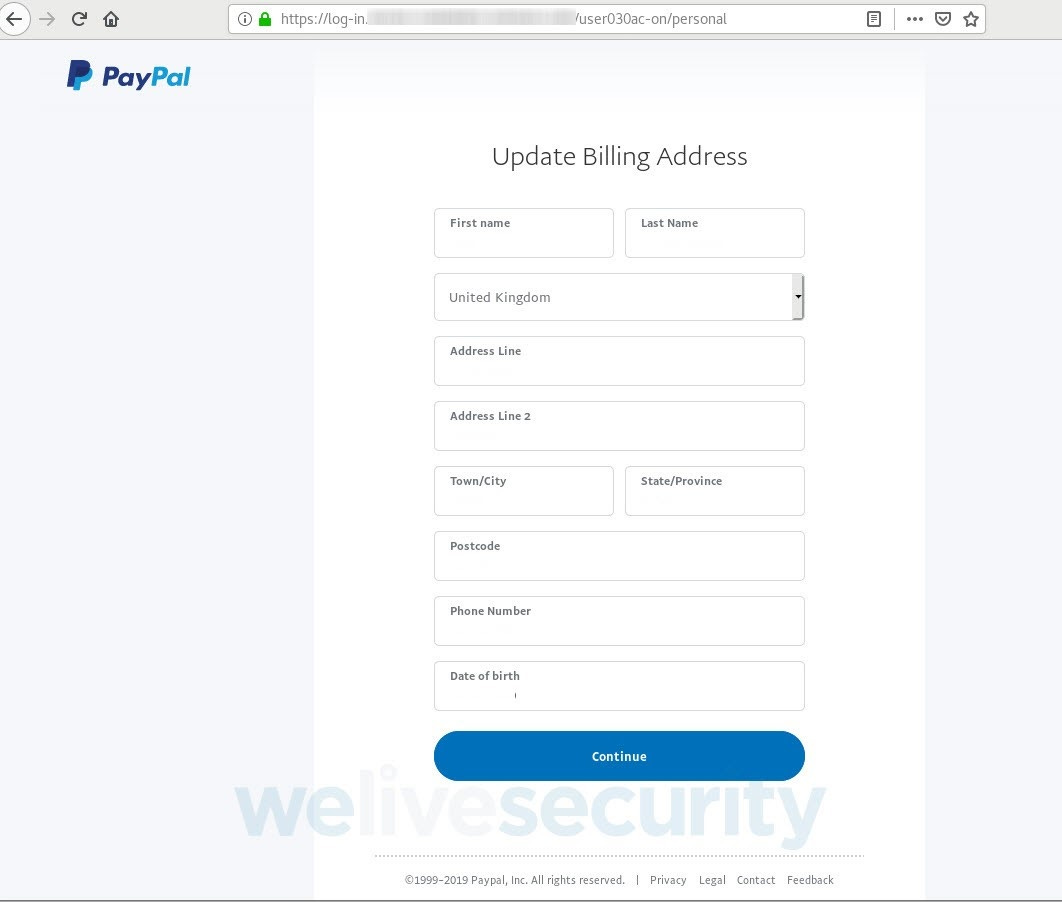
Source: ESET
Now the site asks you to re-enter your credit card details:
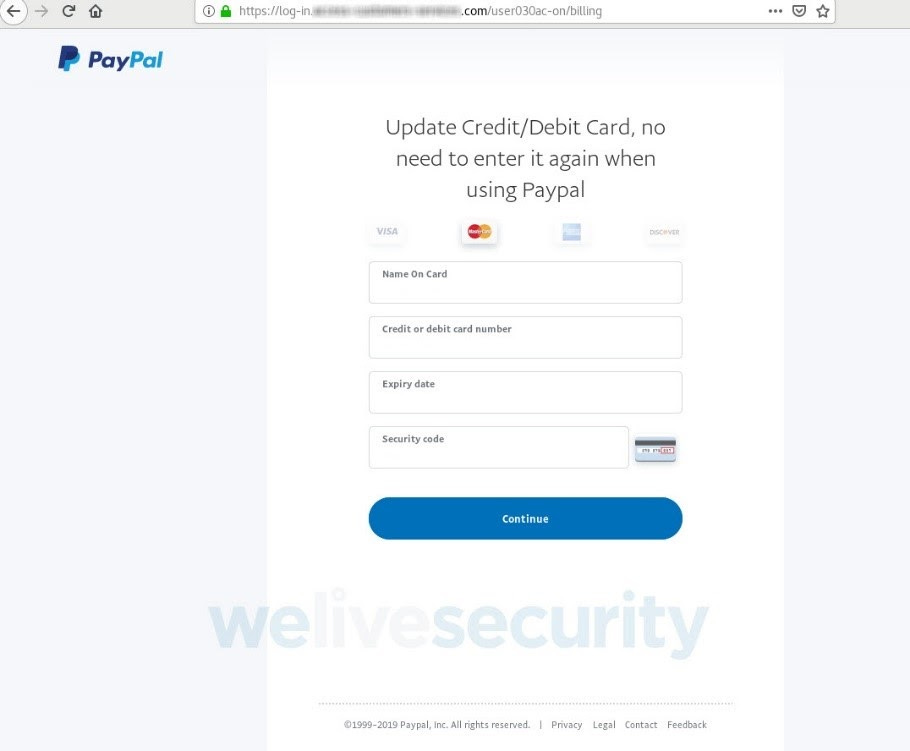
Source: ESET
In order to confirm the validity of this credit card, you apparently need to provide your bank account and routing numbers, along with your mother’s maiden name. Now the alarm bells begin to go off. But you’re curious, so you enter in some bogus information and see where this goes.
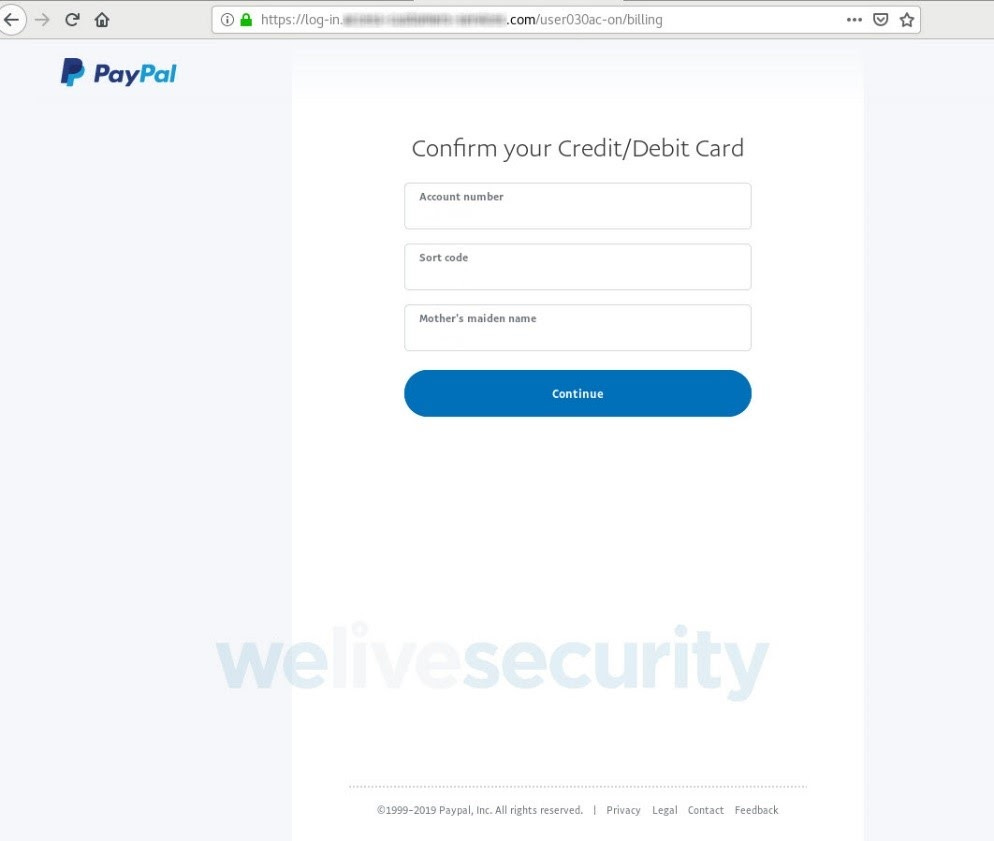
Source: ESET
Whoever owns this site — which clearly isn’t PayPal — now has your PayPal login, your credit card details and corresponding billing address, your bank account info, along with your date of birth and mother’s maiden name. What’s next? Oh, they also want the login to your email account too:
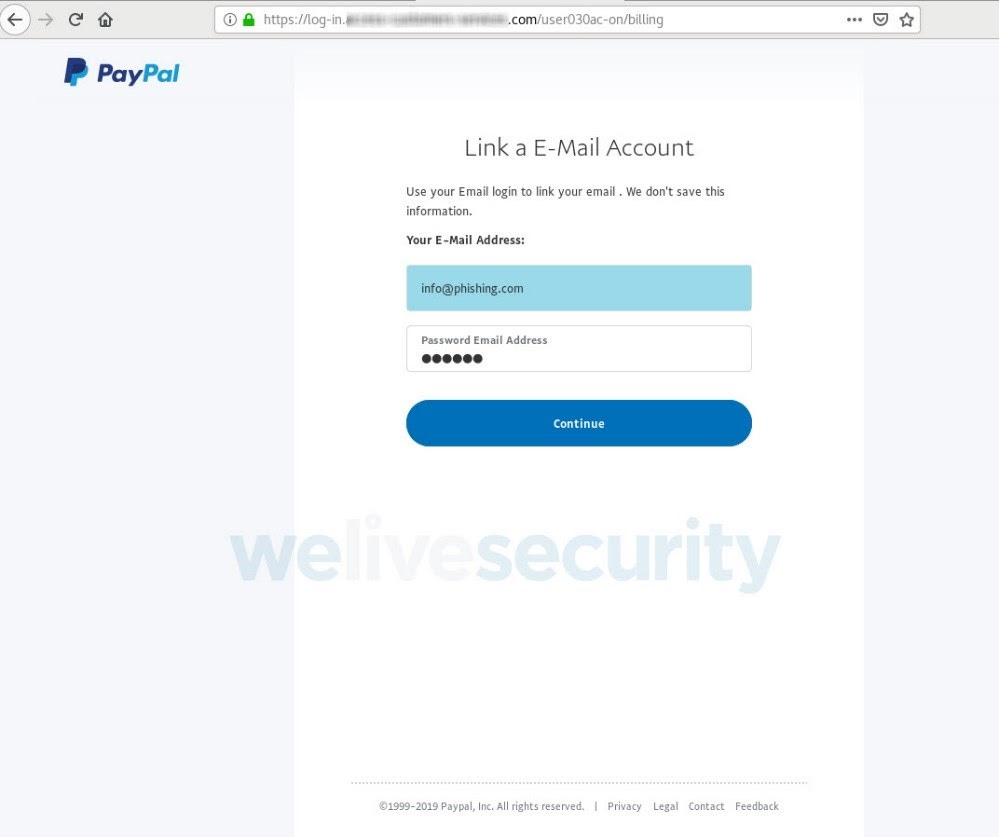
Source: ESET
After all of this, you are finally told that your account has been restored and are redirected back to the real PayPal platform.
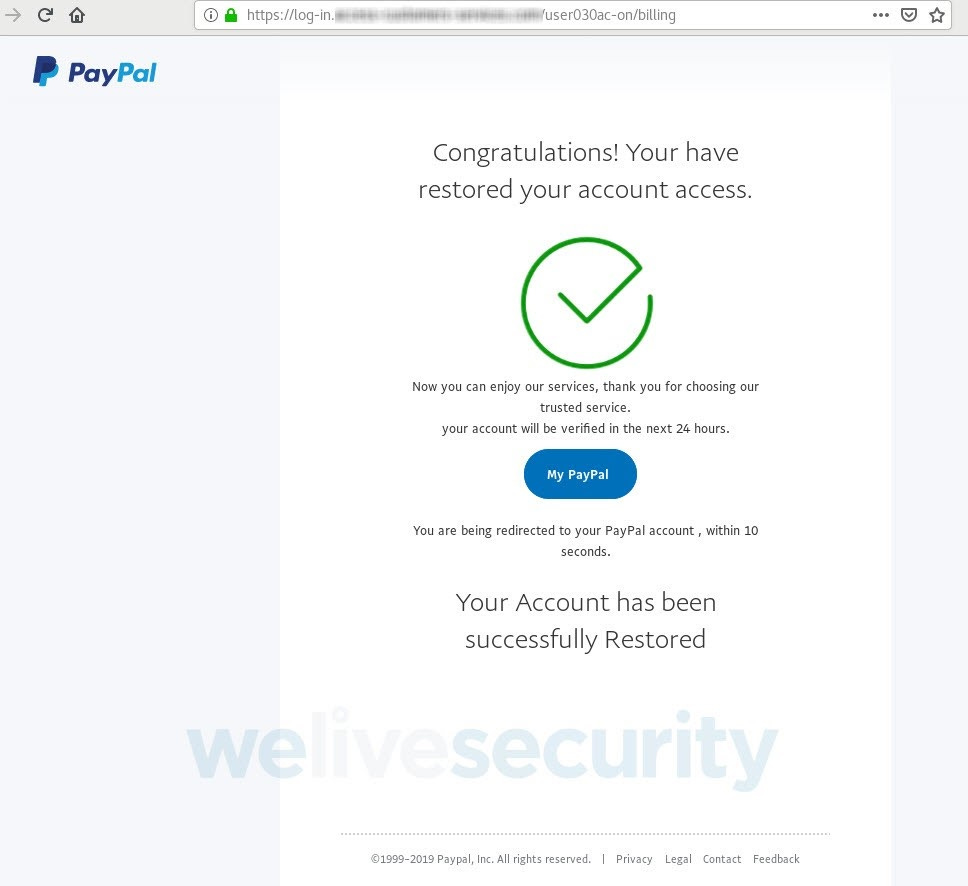
Source: ESET
Unfortunately, you’ve now entrusted a good chunk of your personal and financial data to cybercriminals. Using these details, they can now lock you out of your online accounts, order replacement debit and credit cards to a mailing address of their choosing, access further sensitive information contained in your email inbox, and spend all your money. As if that wasn’t bad enough, they can also use these details to impersonate you and commit all kinds of fraud.
The Larger Scheme at Play
Phishing is one of the oldest and most effective online scams in operation today.
Phishing v.: an attempt to acquire sensitive information about a person online, typically by sending an email that appears to be from a legitimate source, but actually contains a link to a spoofed website that mimics the real one.
The term is derived from the activity of fishing. Just as fishermen use bait to hook fish, cybercriminals use digital bait to hook unsuspecting victims. More often than not, the end goal is monetary gain, which fraudsters can obtain by accessing data such as:
Usernames and passwords
Bank account details
PIN number
Q&A answers (i.e. the answer to ‘What is your mother’s maiden name?’)
Date of birth
Address
According to Valimail, at least 3.4 billion phishing emails are sent around the world each day. Luckily, many of these are automatically detected and wind up in our spam folders. But every now and then, a sophisticated scam will avoid detection filters and trick recipients into handing over their credentials.
How It Works
Most phishers know nothing about their targets. However, they tend to gravitate towards bank and credit card users, those with online marketplace accounts (such as Amazon, Apple, or Ebay), loyalty rewards members, and so on. The most common approach is to spam large email lists in the hope that a small fraction of those email recipients will be unwary enough to fall for this con.
Generally speaking, a phishing campaign tries to get the target to do one of two things:
Download malware. In this case, the scammer casts a wide net by sending an email to users who may or may not use the platform or company being impersonated. In other words, users can receive a message from a bank or other service that they have never used before. Often times, the message includes an attachment or a web link to which users can respond. However, clicking on either one of those commonly results in malicious software, such as ransomware, being installed on their computers.
Hand over sensitive information. In this instance, the scammer will email users who have an account with a specific bank or service provider, making the email far more convincing. The target clicks on a link in the message and is taken to a malicious site designed to resemble the company's webpage. He or she is then prompted to enter their username and password. That data is sent straight to the attacker’s computer, and can now be used to access the victim's account.
From start to finish, the process involves:
Designing the campaign itself. This includes identifying targets, choosing the best brands to spoof, deciding how the phish cycle will work (links versus attachments), and what will be done with the data collected.
Creating the phishing email. This involves everything from setting up email servers, writing content, and creating the malicious links and/or attachments.
Setting up the spoof website. Since phishing involves tricking a person into revealing details such as personal or financial information, the scammer needs to set up a spoofed login page to collect authentication credentials. This process is shown below:
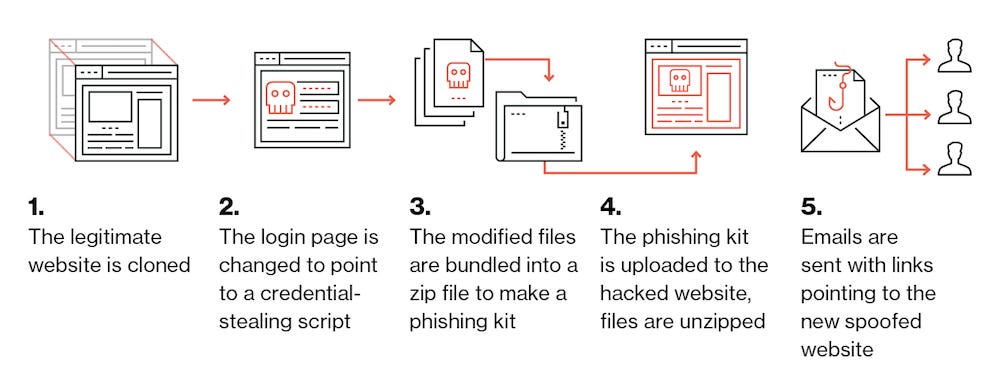
Source: Duo Security
Using the collected data. Upon successful deployment of the phishing campaign, the scammer must now decide whether to sell these credentials on a darknet marketplace or use them to hijack the accounts and make his money that way.
This whole process can be simplified by using a Phishing-as-a-Service platform, which hosts a variety of ready-made tools and campaigns for wannabe criminals to rent. However, we’ll cover this topic, in-depth, at a later time.
Take Steps to Protect Yourself
Phishing attacks come in various shapes and sizes, and are constantly evolving. However, what makes them so successful is that they prey on human weakness. This means that even a momentary lapse in judgment or a minor distraction can have far-reaching and harmful consequences.
To reduce the chance of falling victim to a phishing attack, abide by the following guidelines:
Be smart and use logic while browsing online and checking your email. Resist the urge to click on any links or open any attachments, even if they appear to be from a trusted source. Furthermore, be wary of emails that ask you for sensitive information. Legitimate organizations, including your bank, will never request personal or financial details via email.
Watch out for shortened links. Cybercriminals often use Bit.ly and other URL shortening services to trick users into thinking they are clicking on a legitimate link. Instead, users are inadvertently directed to a fake site. To avoid this, place your mouse over a web link in an email to check whether you’re actually being sent to the right website. When in doubt, log in to the account in question by going to your web browser and typing in the known URL or by doing a simple Google search.
Does that email look suspicious? Read it again. Plenty of phishing emails are obvious. Many of them carry a series of typos, words in all caps, and exclamation marks. They may also have an impersonal greeting, such as Dear Customer or Dear Sir/Madam. This is done intentionally to get past spam filters and weed out those recipients who are too informed to fall for the con.
Be wary of threats and urgent deadlines. Sometimes a reputable company needs you to do something urgently. For example, in 2014, eBay asked its customers to change their passwords quickly after its data breach. However, more often than not, threats and urgency are used by phishers as scare tactics to prompt immediate action by users. These threats may include notices about a fine or advising you to do something to stop your account from being closed. If you receive a message like this, contact the company directly through their website or by phone. Do not trust the links provided in the email.
Final Notes and Updates
Sometimes, a human being can be better at phish filtering than the automated detection of ‘suspicious’ messages by email providers. However, often when it comes to information technology, a sensible and rational person is disadvantaged by a lack of technical know-how. After all, not everyone is interested in the world of bits and bytes.
Phishers rely on victims — who aren’t well-enough informed — to gain access to their lives, both online and offline. Therefore, it is our sincerest hope that by giving readers enough information on this topic, they will be better prepared to sidestep traps designed for the unwary.
Simply put, when it comes to phishing emails, abide by this classic defense strategy: when in doubt, kick it out. Stick with the most basic and effective solutions at your disposal: ignore, delete, and report. This way, you can continue to enjoy your digital life without compromising it.
Useful Resources
Report a phishing attack:
https://www.us-cert.gov/report-phishing
Editor’s Note: Have you been affected by fraud? Most people have, in some form or another. If you have a story you would like to share, we’re sure our readers would benefit from hearing it. Please send an email to editor@theconartist.pub detailing your experience, and we will be in touch. Your privacy and any wishes of anonymity will be respected.
Thanks for reading! If you haven’t already, consider joining our community to receive in-depth exposés on the latest scams, hoaxes, and other forms of fraud.


